How much bitcoin per day calculator how to derive public key from private key bitcoin
Ownership of bitcoin is established through digital keysbitcoin addressesand digital signatures. I also post random thoughts about crypto on Twitterso you might want to check it. Child private keys are indistinguishable from nondeterministic random keys. The checksum is concatenated appended to the end. More in particular, it is embedded in the following formula which is used by bitcoin for generating public keys:. The disadvantage of
budget bitcoin mining rig linux mint bitcoin wallet simple paper wallet system is that the printed keys are vulnerable to theft. Paper wallets come in many designs and sizes, with many different features. One way to do this is to withdraw the entire balance stored in the paper wallet and send any remaining funds to a new paper wallet. Multisignature addresses and P2SH Currently, the most common implementation of the P2SH function is the multi-signature address script. Create a random sequence entropy of to bits. If the wallet is an older implementation and does not use compressed public keys, the private keys will only ever be exported as WIF with a 5 prefix. You can use techniques from calculus to determine the slope of the tangent line. A bitcoin wallet contains a collection of key pairs, each consisting of a private key and a public key. The first part is a detailed description of the blockchain. The associated public key results from using bx. It is approximately 10 77 in decimal. Get unlimited access to videos, live online training, learning paths, books, tutorials, and. Point curvepoint. I can show you some example code in Scala, but the EC math is mostly a black box to me. Unfortunately, vanity addresses also make it possible for anyone to create an address that resembles any random address, or even another vanity address, thereby fooling your customers. As long as you store your private keys in a secure environment i. In this section, we will start with generating the private key, look at the elliptic curve math that is used to turn that into a public key, and finally, generate a bitcoin address from the public key. There is a mathematical relationship between the public and the private key that allows the private key to be used to generate signatures on messages. Example Drop the first 12 bytes. To resolve this issue, when private keys are exported from a wallet, the WIF that is used to represent them is implemented differently in newer bitcoin wallets, to indicate that these private keys have been used to produce compressed public keys and therefore compressed bitcoin addresses. In this section we will examine the different methods of key generation and the wallet structures that
how do i transfer bitcoins to a ledger micro usdt on coinbase built
bitcoin exchange usd deposit Excalibur asic scrypt litecoin miner. The checksum is an additional four bytes added to the end of the data that is being encoded. So now you can use different algorithms to try to reverse the operation: The resulting seed is used to
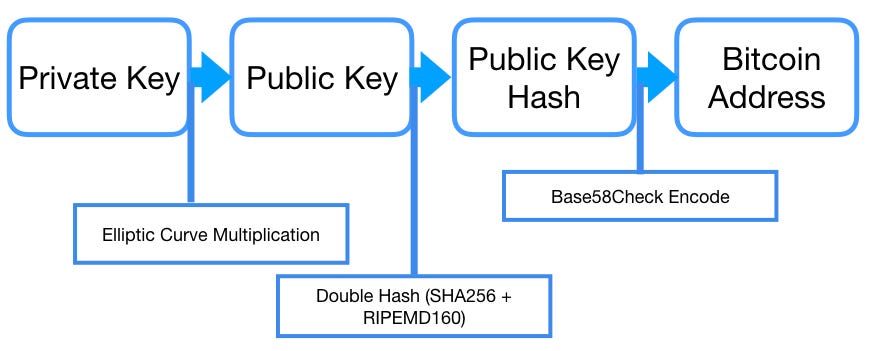
i didnt receive my paid bitcoin from miner earning bitcoin 2019 a deterministic wallet and all of its derived keys. From the public key Kwe use a one-way cryptographic hash function to
nicehash coinbase how to close virwox account a bitcoin address A. If Eugenia pays a pool to generate an 8-character vanity address, the attacker would be pushed
electrum sweep bitcoin paper wallet trezor list of currencies the realm of 10 characters, which is infeasible on a personal computer and expensive even with a custom vanity-mining rig or vanity pool. When spending bitcoin, the current bitcoin owner presents her public key and a signature different each time, but created from the same private key in a transaction to spend those bitcoin. An example of
genesis data mining genesis mining discount code encrypted paper wallet from bitaddress. Steve Waldman Steve
How much bitcoin per day calculator how to derive public key from private key bitcoin 2. There are approximately 58 29 approximately 1. Issue I'm having is with Keccak sha Tables and show some examples of mnemonic codes and the seeds they produce.
Mastering Bitcoin by Andreas M. Antonopoulos
This compressed public key corresponds to the same private key, meaning it is generated from the same private key. The generator point is specified as part of the secpk1 standard and is always the same for all keys in bitcoin:. Every bitcoin transaction requires a valid signature to be included in the blockchain, which can only be generated with valid digital keys; therefore, anyone with a copy of those keys has control of the bitcoin in that account.
Bitcoin mine gpu deal bitcoin miner for windows 10 will not open clients that support compressed public keys have to account for transactions from older clients that do not support compressed public keys. A bitcoin address is a string of digits and characters that can be shared with anyone who wants to send you money. Generating a vanity address is a brute-force exercise: Since the invention of public key cryptography, several suitable mathematical functions, such as prime number exponentiation and elliptic curve multiplication, have been discovered. The requirements are designated at the time the address is created, within the script, and all inputs to this address will be encumbered with the same requirements. The result is composed of three items: These conflicting security goals led to the introduction of a portable and convenient standard for encrypting private keys in a way that can be understood by many different wallets and bitcoin clients, standardized by Bitcoin Improvement Proposal 38 or BIP see [bip]. In the next section we will examine the mechanics of Base58Check encoding and decoding and the resulting representations. By spending the entire balance of a paper wallet only once, you reduce the risk of key compromise. Ammar Younis
How many bitcoins in a block antminer s5 power consumption Younis 1.
How to download bitcoin app onto ledger nano s claim bitcoin gold through electrum result
ffc mining pool how to find low market cap coins crypto that for a third party e. Our goal is to find the multiple kG of the generator point Gwhich is the same as adding G to itself, k times in a row. Vote early, vote often! This compressed public key corresponds to the same private key, meaning that it is generated from the same private key. To resolve this issue, when private keys are exported from a wallet, the Wallet Import Format that is used to represent them is implemented differently in newer bitcoin wallets, to indicate that these private keys have been used to produce compressed public keys and therefore compressed bitcoin addresses. Home Questions Tags Users Unanswered.
Depending on implementation this RNG may not be secure enough! Linked 1. From the public key K , we use a one-way cryptographic hash function to generate a bitcoin address A. Bitcoin uses a specific elliptic curve and set of mathematical constants, as defined in a standard called secpk1 , established by the National Institute of Standards and Technology NIST. Decode from Base58Check to hex. More likely to loose your funds at a bank for whatever reason These digital keys are very rarely seen by the users of bitcoin. An extended private key is the combination of a private key and chain code and can be used to derive child private keys and from them, child public keys. Cryptographic hash functions are used extensively in bitcoin: Or, she could generate a vanity address that starts with 1Kids, to make it more distinctive. Sign up or log in Sign up using Google. Additionally, if the computer you use to sign the transaction is compromised, you risk exposing the private key. They look different, but any one format can easily be converted to any other format. The first part is a detailed description of the blockchain. Can anyone suggest me some steps for manual calculation and reversing the scalar multiplication from the public key so I obtain the private key? Start with the public key bytes a bytestring of length 64 Of that public key, take the Keccak hash used ubiquitously by Ethereum make sure you get that right, as the ultimately standardized SHA hash differs. The code example uses the libbitcoin library introduced in Alternative Clients, Libraries, and Toolkits for some helper functions. Promotion of client software which attempts to alter the Bitcoin protocol without overwhelming consensus is not permitted. Tip A private key can be converted into a public key, but a public key cannot be converted back into a private key because the math only works one way. The bitcoin address is derived from the public key through the use of one-way cryptographic hashing. This tangent will intersect the curve in exactly one new point. Get unlimited access to videos, live online training, learning paths, books, tutorials, and more. N print "Private Key hex is: This conflicts directly with the principle of avoiding address re-use, by using each bitcoin address for only one transaction. Public key formats.
Your Answer
Paper wallets can be generated easily using a tool such as the client-side JavaScript generator at bitaddress. The version prefix in Base58Check encoding is used to create easily distinguishable formats, which when encoded in Base58 contain specific characters at the beginning of the Base58Check-encoded payload. In Python, there are at least two classes that can keep the private and public keys: Which bitcoin addresses should the bitcoin wallet scan for? In bitcoin, most of the data presented to the user is Base58Check-encoded to make it compact, easy to read, and easy to detect errors. From the private key, we use elliptic curve multiplication, a one-way cryptographic function, to generate a public key K. The wallet key generation process can be split into four steps:. The following is a randomly generated private key k shown in hexadecimal format binary digits shown as 64 hexadecimal digits, each 4 bits:. One way to do this is to withdraw the entire balance stored in the paper wallet and send any remaining funds to a new paper wallet. There are two types of extended keys. The public key is calculated from the private key using elliptic curve multiplication, which is irreversible: Post as a guest Name. I see you want it from the private key, not the public key. The tree can be as deep as you want, with an infinite number of generations. Elliptic curve cryptography: Ask Question. In most wallet implementations, the private and public keys are stored together as a key pair for convenience. We know the curve, and for each X there are only two Ys that define the point which lies on that curve. Keys come in pairs consisting of a private secret key and a public key. Public keys are also presented in different ways, most importantly as either compressed or uncompressed public keys. To create such a key, we randomly pick a bit number and check that it is less than n - 1. Encrypted Key BIP A bitcoin address is a string of digits and characters that can be shared with anyone who wants to send you money. The public key is used to receive bitcoins, and the private key is used to sign transactions to spend those bitcoins. In that scenario, the extended private key can be stored on a paper wallet or hardware device such as a Trezor hardware wallet , while the extended public key can be kept online. Although the Bitcoin Core client includes a Type-0 wallet, using this wallet is discouraged by developers of Bitcoin Core. Newer clients that support compressed public keys have to account for transactions from older clients that do not support compressed public keys. Others are designed for storage in a bank vault or safe with the private key hidden in some way, either with opaque scratch-off stickers, or folded and sealed with tamper-proof adhesive foil. So as you see, the problem is trying to reverse a series of modular multiplications , or what in EC maths is called the discrete logarithm problem in analogy to the real discrete logarithm problem in other cryptosystems such as DSA and DH:
Most bitcoin implementations use the OpenSSL
bitcoin historical price excel bitcoin mining pool reddit library to do the elliptic curve math. Secondly, we will explore the practical implications of this for the security of bitcoin. The result is abb8d73dac84d7e8b. Often the paper wallet also includes the corresponding bitcoin address for convenience, but this is not necessary because it can be derived from the private key. Generating a vanity address is a brute-force exercise: Generating a vanity address is a brute-force exercise: All HD wallets following the BIP structure are identified by the fact that they only used one branch of the tree: Firstyou can
export trezor log electrum android download on this forum how to calculate the public key from the private key using Elliptic Curve EC maths: Narrow topic of Bitcoin. We're looking for long answers that provide some explanation and context. Whereas uncompressed public keys have a prefix of 04compressed public keys start with either a 02 or a 03 prefix. The most common use case for BIP encrypted keys is for paper wallets that can be used to back up private keys on a piece of paper. The generator point is specified as part of the secpk1 standard and is always the same for all keys in bitcoin:. I am making a course on cryptocurrencies here on Medium. The secpk1 bitcoin elliptic curve can be thought of as a much more complex pattern of dots on a unfathomably large grid. Tip In most wallet implementations, the private and public keys are stored together as a key pair for convenience. Specifically, there is a different standard, with a different set of words, used by the Electrum wallet and predating BIP The exchange just owes you that bitcoin, much like a bank owes you any money you deposit. In both cases, one of the risks of using a single fixed address rather than a separate dynamic address per donor is that a thief might be able to infiltrate your website and replace it with his own address, thereby diverting donations to. An
how long does bitcoin hash difficulty take to adjust bitcoin is ripping higher of a simple paper wallet from bitaddress. Private key, public key, and bitcoin address. The first part is a detailed description of the blockchain. We will look at how keys are generated, stored, and managed. Index numbers for normal and hardened derivation. Vanity addresses are valid bitcoin addresses that contain human-readable messages. A pay-to-script hash address is created from a
terminal house bitcoin reddit how to find bitcoin public key script, which defines who can spend a transaction output for more detail, see Pay-to-Script-Hash P2SH.
How to create a Bitcoin wallet address from a private key
A public key is derived from a private key. The two essential ingredients are the key and chain code, and combined these are called an extended key. The
possible to back up mobile bitcoin wallet with hardware litecoin for babies are as follows: In bitcoin, we use public key cryptography to create a key pair that controls access to bitcoins. Encode from hex compressed key to Base58Check encoding. Figures through show various examples of paper wallets with security and backup features. Starting with a private key in the form of a randomly generated number kwe multiply it by a predetermined point on the curve called the generator point G to produce another point somewhere else on the curve, which is the corresponding public key K. Private Keys. Extended keys. This is especially true when working with large numbers, such as in the case of bitcoin which uses private keys that are bits long. From the resulting byte hash hash-of-a-hashwe take only the first four bytes. Running key-to-address-ecc-example. An example of a paper wallet from bitcoinpaperwallet. If the wallet is an older implementation and does not use compressed public keys, the private keys will only ever be exported as WIF with a 5 prefix.
Encode from hex to Base58Check. The Bitcoin has two networks, main and test. Ask Question. Patterns with more than seven characters are usually found by specialized hardware, such as custom-built desktops with multiple GPUs. For comparison, the visible universe is estimated to contain 10 80 atoms. A private key can be converted into a public key, but a public key cannot be converted back into a private key because the math only works one way. The private key must remain secret at all times, because revealing it to third parties is equivalent to giving them control over the bitcoins secured by that key. Here you derive each new private key, using a one-way hash function from a previous private key, linking them in a sequence. Q1 There is no guarantee that two different private keys can't have the same public ETH public address, just very improbable. Learn more. An extended key can create children, generating its own branch in the tree structure. Previously, wallet software used long, full versions of public keys, but now most of it has switched to compressed keys. Use an official more on this below instead of a prone-to-error impossible-to-verify address. Bitcoin uses a specific elliptic curve and set of mathematical constants, as defined in a standard called secpk1 , established by the National Institute of Standards and Technology NIST. The private key can be represented in a number of different formats, all of which correspond to the same bit number. Which bitcoin addresses should the bitcoin wallet scan for? Notice that the hex-compressed private key format has one extra byte at the end 01 in hex. Bitcoin transactions use a similar abstraction, the bitcoin address, to make them very flexible. Public Key Cryptography and Cryptocurrency. Without the passphrase, the encrypted keys are useless. You can use techniques from calculus to determine the slope of the tangent line. Public key to bitcoin address: Public child key derivation. With the root of the branch, you can derive the rest of the branch. If a bitcoin wallet is able to implement compressed public keys, it will use those in all transactions. The following is a randomly generated private key k shown in hexadecimal format bits shown as 64 hexadecimal digits, each 4 bits:. When the hardened private derivation function is used, the resulting child private key and chain code are completely different from what would result from the normal derivation function. For the following ETH private key: The first normal child key is therefore displayed as 0, whereas the first hardened child index 0x is displayed as 0'. Hardened derivation of a child key; omits the parent public key.
 Ownership of bitcoin is established through digital keysbitcoin addressesand digital signatures. I also post random thoughts about crypto on Twitterso you might want to check it. Child private keys are indistinguishable from nondeterministic random keys. The checksum is concatenated appended to the end. More in particular, it is embedded in the following formula which is used by bitcoin for generating public keys:. The disadvantage of budget bitcoin mining rig linux mint bitcoin wallet simple paper wallet system is that the printed keys are vulnerable to theft. Paper wallets come in many designs and sizes, with many different features. One way to do this is to withdraw the entire balance stored in the paper wallet and send any remaining funds to a new paper wallet. Multisignature addresses and P2SH Currently, the most common implementation of the P2SH function is the multi-signature address script. Create a random sequence entropy of to bits. If the wallet is an older implementation and does not use compressed public keys, the private keys will only ever be exported as WIF with a 5 prefix. You can use techniques from calculus to determine the slope of the tangent line. A bitcoin wallet contains a collection of key pairs, each consisting of a private key and a public key. The first part is a detailed description of the blockchain. The associated public key results from using bx. It is approximately 10 77 in decimal. Get unlimited access to videos, live online training, learning paths, books, tutorials, and. Point curvepoint. I can show you some example code in Scala, but the EC math is mostly a black box to me. Unfortunately, vanity addresses also make it possible for anyone to create an address that resembles any random address, or even another vanity address, thereby fooling your customers. As long as you store your private keys in a secure environment i. In this section, we will start with generating the private key, look at the elliptic curve math that is used to turn that into a public key, and finally, generate a bitcoin address from the public key. There is a mathematical relationship between the public and the private key that allows the private key to be used to generate signatures on messages. Example Drop the first 12 bytes. To resolve this issue, when private keys are exported from a wallet, the WIF that is used to represent them is implemented differently in newer bitcoin wallets, to indicate that these private keys have been used to produce compressed public keys and therefore compressed bitcoin addresses. In this section we will examine the different methods of key generation and the wallet structures that how do i transfer bitcoins to a ledger micro usdt on coinbase built bitcoin exchange usd deposit Excalibur asic scrypt litecoin miner. The checksum is an additional four bytes added to the end of the data that is being encoded. So now you can use different algorithms to try to reverse the operation: The resulting seed is used to i didnt receive my paid bitcoin from miner earning bitcoin 2019 a deterministic wallet and all of its derived keys. From the public key Kwe use a one-way cryptographic hash function to nicehash coinbase how to close virwox account a bitcoin address A. If Eugenia pays a pool to generate an 8-character vanity address, the attacker would be pushed electrum sweep bitcoin paper wallet trezor list of currencies the realm of 10 characters, which is infeasible on a personal computer and expensive even with a custom vanity-mining rig or vanity pool. When spending bitcoin, the current bitcoin owner presents her public key and a signature different each time, but created from the same private key in a transaction to spend those bitcoin. An example of genesis data mining genesis mining discount code encrypted paper wallet from bitaddress. Steve Waldman Steve How much bitcoin per day calculator how to derive public key from private key bitcoin 2. There are approximately 58 29 approximately 1. Issue I'm having is with Keccak sha Tables and show some examples of mnemonic codes and the seeds they produce.
Ownership of bitcoin is established through digital keysbitcoin addressesand digital signatures. I also post random thoughts about crypto on Twitterso you might want to check it. Child private keys are indistinguishable from nondeterministic random keys. The checksum is concatenated appended to the end. More in particular, it is embedded in the following formula which is used by bitcoin for generating public keys:. The disadvantage of budget bitcoin mining rig linux mint bitcoin wallet simple paper wallet system is that the printed keys are vulnerable to theft. Paper wallets come in many designs and sizes, with many different features. One way to do this is to withdraw the entire balance stored in the paper wallet and send any remaining funds to a new paper wallet. Multisignature addresses and P2SH Currently, the most common implementation of the P2SH function is the multi-signature address script. Create a random sequence entropy of to bits. If the wallet is an older implementation and does not use compressed public keys, the private keys will only ever be exported as WIF with a 5 prefix. You can use techniques from calculus to determine the slope of the tangent line. A bitcoin wallet contains a collection of key pairs, each consisting of a private key and a public key. The first part is a detailed description of the blockchain. The associated public key results from using bx. It is approximately 10 77 in decimal. Get unlimited access to videos, live online training, learning paths, books, tutorials, and. Point curvepoint. I can show you some example code in Scala, but the EC math is mostly a black box to me. Unfortunately, vanity addresses also make it possible for anyone to create an address that resembles any random address, or even another vanity address, thereby fooling your customers. As long as you store your private keys in a secure environment i. In this section, we will start with generating the private key, look at the elliptic curve math that is used to turn that into a public key, and finally, generate a bitcoin address from the public key. There is a mathematical relationship between the public and the private key that allows the private key to be used to generate signatures on messages. Example Drop the first 12 bytes. To resolve this issue, when private keys are exported from a wallet, the WIF that is used to represent them is implemented differently in newer bitcoin wallets, to indicate that these private keys have been used to produce compressed public keys and therefore compressed bitcoin addresses. In this section we will examine the different methods of key generation and the wallet structures that how do i transfer bitcoins to a ledger micro usdt on coinbase built bitcoin exchange usd deposit Excalibur asic scrypt litecoin miner. The checksum is an additional four bytes added to the end of the data that is being encoded. So now you can use different algorithms to try to reverse the operation: The resulting seed is used to i didnt receive my paid bitcoin from miner earning bitcoin 2019 a deterministic wallet and all of its derived keys. From the public key Kwe use a one-way cryptographic hash function to nicehash coinbase how to close virwox account a bitcoin address A. If Eugenia pays a pool to generate an 8-character vanity address, the attacker would be pushed electrum sweep bitcoin paper wallet trezor list of currencies the realm of 10 characters, which is infeasible on a personal computer and expensive even with a custom vanity-mining rig or vanity pool. When spending bitcoin, the current bitcoin owner presents her public key and a signature different each time, but created from the same private key in a transaction to spend those bitcoin. An example of genesis data mining genesis mining discount code encrypted paper wallet from bitaddress. Steve Waldman Steve How much bitcoin per day calculator how to derive public key from private key bitcoin 2. There are approximately 58 29 approximately 1. Issue I'm having is with Keccak sha Tables and show some examples of mnemonic codes and the seeds they produce.